The ultimate test of the security operations center
Netleaf: Cyber Defence Center
Welcome to Netleaf: Cyber Defence Center, a strategic board game where players compete to build and secure their cyber infrastructure while blocking threats and outsmarting opponents. In this immersive game, you’ll navigate the intricate world of cyber security, constructing log collectors, establishing operations rooms, and acquiring valuable support cards to gain an edge. But beware, as hackers lurk and dice rolls can tip the balance of power. Engage in sharp card trading, deploy shortcuts, and leverage your network security expertise to emerge victorious in Netleaf: Cyber Defence Center.emergin
Game info and rules
The point of the game is to get 10 victory points. You get points by building log collectors, operations rooms, getting the biggest network or workforce, and buying support cards.
Game Components
- 19 IT hexes
- 9 empty border hexes
- 9 special border hexes
- 18 circular number tokens
- 95 component cards (with symbols of honeypots, SIEM, IDR and network sensors)
- 26 support cards (14 SOC engineer cards, 5 security cards, 6 shortcut cards)
- 4 building cost cards
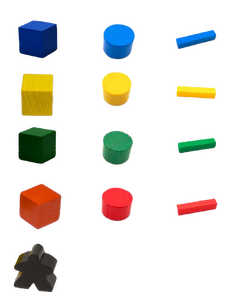
- 2 award cards: biggest network and biggest work force
- 16 operations rooms (4 of each color)
- 16 log collectors (4 of each color)
- 60 cables (15 of each color)
- 2 dice
- 1 hacker
Constructing the board
The border hexes play a crucial role in anchoring the board and maintaining its stability. Before proceeding to build the interior, ensure that you consistently transition the border hexes from being empty to containing a component.
Begin by arranging all the component hexes with their black side facing up on the table. Then, take turns selecting one and positioning it within the border.
Once the board is structured, proceed similarly with the circular numbers. Place them all with their black side up and take turns situating them on the table.
Bank
The player that rolled the lowest dice in the beginning o the game becomes the bank. That person has the responsibility to give the necessary cards everytime the dice rolls. He/or she should also make sure that everyone pas the correct amount when they buy or trade something.
Starting the game

To determine the starting player, each player rolls two dice. The player achieving the highest total begins the game. In the initial round, each player positions a log collector and a cable at a junction between two or three hexes. Following this, with your first two log collectors in place, you may lay a cable.
The size of the number is linked to the likelihood of rolling the number, the bigger the number the large the chance.
Once the log collectors are set, players can proceed to lay cables. Afterwards, the process repeats, starting from the last player. Players retrieve cards corresponding to their final log collector placement.
Important: log collectors must be built at least two cables apart, and the initial cables must not intersect.
Once all players have positioned two log collectors and two cables, the game begins. Roll the dice to determine which cards you receive. For instance, if your log collector is adjacent to a SIEM marked with a number 9 and the dice yields a 9, you acquire a corresponding SIEM card from the bank.
7
When a player rolls a 7, they have the opportunity to position the hacker on any numbered space on the board. Those holding more than 7 cards are required to return half of their cards to the bank. If the total number of cards is odd, players must surrender the smaller portion.
The player who rolled a 7 can select a card from the player whose log collector or operations room is adjacent to a component hex border.
If a players number is covered by the hacker, they do not receive any component cards until the hacker is relocated.
Each time someone rolls a 7, the hacker must change positions. For instance, if the hacker was positioned on number 9 on a SIEM hex, it must be moved elsewhere, such as number 8 on an endpoint hex.
We begin the game by placing the hacker on the middle hex, the black one with the Netleaf icon on it.
Game Pieces
Cables
To construct a log collector, you must first establish cables. Once two cables are laid down, you gain permission to erect a log collector. Each cable installation requires a network sensor and an IDR. Upon connecting five cables, you qualify to obtain the longest network card, which is worth 2 points. However, if another player builds a larger network, they acquire the card instead.
Log collector
Begin by establishing log collectors, with the first two being set up before the game commences. For additional details, refer to the provided resource. To construct your third and fourth log collectors, you must compensate the bank with a network sensor, IDR, honeypot, and a SIEM card.
Each log collector contributes one victory point to your total.
Operations room
Once you’ve constructed the log collector, you have the option to upgrade it into an operations room by providing 3 SOAR and 2 SIEM cards.
If you possess an operations room and a nearby number is rolled, you receive two component cards instead of one.
Each operations room adds 2 victory points to your total.
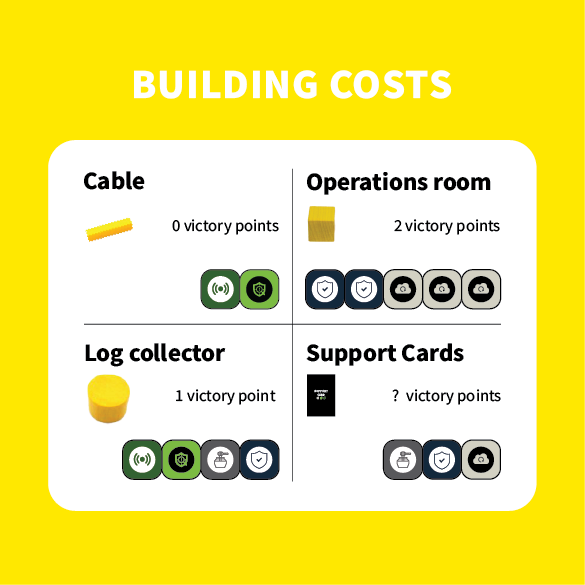
Support card
Purchasing support cards grants you access to SOC engineers, shortcuts, or security cards, each offering distinct advantages in the game.
Support cards can only be utilized during your turn and prior to rolling the dice.
SOC Engineer
Using your SOC engineer card enables you to relocate the hacker to a number of your preference.
Upon acquiring 3 SOC engineer cards, you obtain the largest workforce card. However, if another player possesses more SOC engineer cards than you, the card transfers to that player.
When you buy a SOC card you can play them when it is your turn but you need to start with that card. After you have used the card you have to lay them down in front of you for the rest of the game and are not able to reuse them.
Shortcuts
Three distinct shortcut cards offer unique advantages:
- Alt 4: Allows you to claim all resource cards of a specified type from other players.
- Ctrl C + Ctrl V: Enables you to place 2 cables.
- Ctrl Shift Esc: Grants you the ability to select 2 resource cards of your choice from the bank.
Security
Obtaining any of the 5 security cards earns you a point:
- Cloud Security
- Email Security
- Firewall
- NAC (Network Access Control)
- Remote Access

Trade
During your turn, you have the option to engage in card trading with other players or with the bank.
When trading with a player, both parties can exchange specific cards. For instance, you might swap 1 SIEM for 1 SOAR, or negotiate alternative exchange rates such as 1 SIEM for 2 SOAR. Exercise caution and strategize your trades wisely.
Alternatively, trading with the bank involves offering 4 identical cards in exchange for 1 specific card. However, if you have a log collector or an operations room positioned by the border, you can enhance your trading power. In such cases, you can trade 2 for 1 specific card or 3 for 1 card of your choice, depending on the hex where your log collector or headquarters is situated.
How to win
The main goal of the game is to gather 10 points. You do this by buying support cards, operations rooms and log collectors and/or gaining the largest network and/or workforce. The player that reaches the 10 points first wins.
Dictionary
Email Security
Email security is safeguarding your email accounts and messages from unauthorized access, theft, or malicious attacks.
Cloud Security
Cloud security is like a combination of high-tech locks, firewalls, and alarms for your data and apps in the cloud, constantly on guard against hacking attempts, data leaks, and outages.
Remote access
Remote access security is like a secure bridge between your device and the network, ensuring only authorized users can cross and protecting sensitive information during the journey.
Firewall
A firewall acts like a security guard at your network’s entrance, checking incoming and outgoing traffic to block anything suspicious and only allowing safe connections.
Network Access Control
Network Access Control (NAC) is like a bouncer at a high-security club for your network, only letting in devices that meet specific criteria and keeping out any unauthorized or risky ones.
Penetration tester
A penetration tester, also called a pen tester, is a cyber security professional who ethically hacks into a computer system or network to find vulnerabilities before malicious actors can exploit them.
SOC analyst
Reacts to alerts generated by security tools, investigating potential incidents and taking steps to contain them. Imagine a lookout who identifies and investigates smoke on the horizon.
Threat hunter
Proactively searches for hidden threats within a network, using their knowledge and analytical skills to uncover potential attacks before they happen. Think of a detective who investigates suspicious activity even before any alarms are triggered.
SOC Engineer
A SOC engineer is the tech whiz of the security team, building and maintaining the tools analysts use to fight cyber threats.
Alt F4
This is a keyboard shortcut that closes the currently active window on your computer.
CTRL C + CTRL V
Ctrl C is used to copy highlighted text, images, or files, while Ctrl V pastes the copied content wherever your cursor is positioned
CTRL SHIFT ESC
Ctrl Shift Esc is a keyboard shortcut that launches the Task Manager on your computer. This tool lets you manage running applications, processes, and system resources.
