Actionable 360° Intelligence
Cyber Threat Intelligence
Cyber threats don’t strike out of the blue — they develop quietly over time, often in places that are hard to see. That’s where Netleaf’s Cyber Threat Intelligence (CTI) comes in. Our service helps you understand what threats are out there, how they work, who’s behind them — and most importantly, how to stop them before they cause harm.
Instead of reacting after an incident, CTI empowers you to act early. We help you spot potential attackers, uncover weak points in your digital footprint, and take proactive steps to protect your organisation.
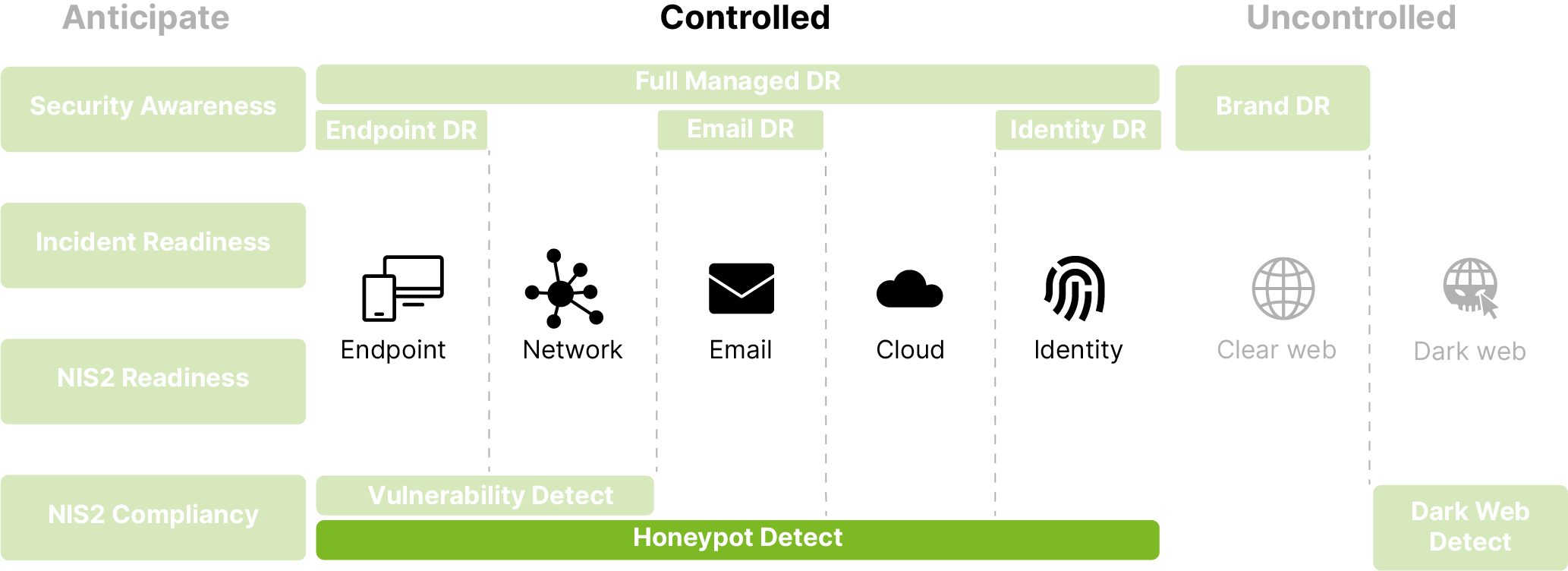
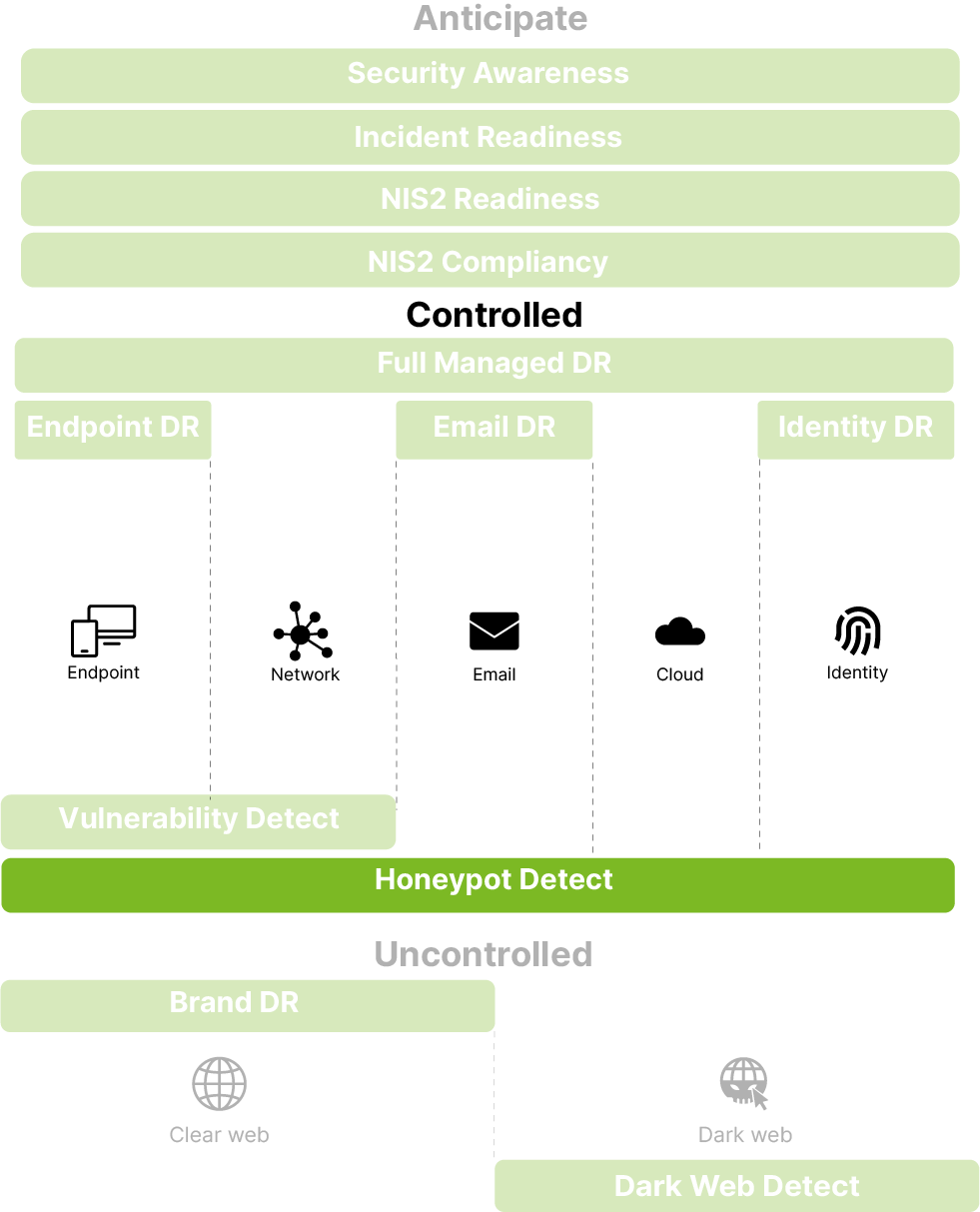
Why choose our Cyber Threat Intelligence
Your organisation is more connected than ever — which means your risk extends beyond your own network. Public websites, suppliers, partners, and even social media accounts can all become attack surfaces for cybercriminals.
Our Cyber Threat Intelligence service helps you:
• Detects threats before they reach your network
• Protects your brand, employees, and customers against digital risks
• Tracks phishing, impersonation, and data leaks across the deep, dark, and surface web
• Gives you actionable alerts — not just raw data
• Operated by experts who validate and investigate every lead
• Integrated with your existing cybersecurity processes
• Continuously monitors your digital footprint and threat exposure
• Helps you meet compliance and risk management requirements
• Backed by forensic tools, sandboxing, and custom threat hunting
We don’t just deliver data — we deliver insight, context, and action.
Which Cyber Threat Intelligence services do we provide?
We break our service down into three easy-to-understand building blocks.
Threat Intelligence (TI)
Cyber threats don’t start with a breach — they often begin in the shadows.
Our Threat Intelligence service gives you visibility into the hidden corners of the internet where cybercriminals operate: underground forums, ransomware leak sites, encrypted messaging channels, and illicit marketplaces. These are not indexed by search engines and are intentionally concealed from the public web — but they’re where stolen data is traded, company names are discussed, and future attacks are planned.
By continuously monitoring these environments, we help you stay one step ahead of emerging risks. You’ll be alerted when:

Employee credentials (such as emails and passwords) are leaked or sold

Your company name is mentioned in malicious discussions or threat actor chatter

Ransomware gangs publish data stolen from your business or supply chain
With real-time insights and actionable alerts, our local experts help you take proactive steps to reduce risk — before a leak becomes a crisis.
Digital Risk Protection (DRP)
Cybercriminals often misuse trusted brands to launch phishing campaigns, create fake websites, or impersonate company accounts on social media. These attacks don’t just target your business — they target your customers, employees, and reputation.
Our Digital Risk Protection service helps you detect and act on brand abuse across the public web. We monitor for:

Fake websites and login pages that mimic your brand

Impersonated social media accounts targeting your audience

Lookalike domains used for phishing or fraud

Misuse of your brand name or logo in ads, apps, or content
When threats are detected, we alert you and assist in fast takedown procedures — limiting exposure and preventing damage.
Attack Surface Management (ASM)
This is like a digital security check-up. We look at what parts of your IT environment are publicly visible or could be misused by hackers — even if you weren’t aware of them.

Forgotten websites, subdomains, dangling dns records

Misconfigured systems or old software that need updates

Development environments accidentally left open to the internet

Weak points in your email security settings

Cyber threats don’t start with a breach — they often begin in the shadows.
Our Threat Intelligence service gives you visibility into the hidden corners of the internet where cybercriminals operate: underground forums, ransomware leak sites, encrypted messaging channels, and illicit marketplaces. These are not indexed by search engines and are intentionally concealed from the public web — but they’re where stolen data is traded, company names are discussed, and future attacks are planned.

Cybercriminals often misuse trusted brands to launch phishing campaigns, create fake websites, or impersonate company accounts on social media. These attacks don’t just target your business — they target your customers, employees, and reputation.
Our Digital Risk Protection service helps you detect and act on brand abuse across the public web.

This is like a digital security check-up. We look at what parts of your IT environment are publicly visible or could be misused by hackers — even if you weren’t aware of them.
How it works
We combine automated threat collection with human-led investigation to give you a complete, actionable view of the cyber threats facing your organisation.
Our system continuously scans the open, deep, and dark web for mentions of your brand, domain names, executives, leaked credentials, and more. Once potential threats are identified, our analysts validate them and connect the dots — linking IOCs with relevant campaigns, actors, or known attack patterns.
From phishing kits targeting your company to leaked databases or impersonation attempts, every alert is assessed and enriched before it reaches you. You receive clear, prioritized intelligence with recommendations on how to respond, whether that means blocking an IP, taking down a malicious domain, or warning your users.
Ready to see what others overlook?
Cyber threats don’t wait — and neither should you. With Netleaf’s Cyber Threat Intelligence, you gain the visibility, context, and expert support you need to act with confidence. Whether you’re looking to protect your brand, secure your supply chain, or simply stay ahead of the next breach, we’re here to help.
Let’s uncover what’s hiding in the shadows — together.
Contact us today to learn how Cyber Threat Intelligence can strengthen your security strategy.
